DDACS 2.0.1 Getting Started Guide
This manual provides quick-start guidance to DDACS Windows endpoint protection suite
version 2.0.1
Installing DDACS
Installation
of DDACS is easy.
Download a self-extracting installer package suitable for your
operating
system, run it and follow the installation instructions. The
installation asks
only two questions:
- About installation
directory (default is "c:\Program Files\DDACS" or "c:\Program Files (x86)\DDACS" for 64-bit OS)
- If you want to
start DDACS automatically
If
you ever want to uninstall DDACS, follow the procedure below.
- Open
DDACS Command Prompt and run "ff -ra" in order to disable DDACS
self-protection. You will be asked for administration password, input
it in order to proceed
- Run "uninstall-ddacs.exe"
from command prompt or
"Uninstall" from DDACS
start menu
- When asked to reboot, do
it in order to complete uninstallation
Using DDACS
This chapter describes DDACS
essentials and configuration
tools and files.
DDACS Control Panel (GUI)
DDACS Control Panel is
the most
convenient way to create and
manipulate rules. It has tabs for all features included in the
installed edition (please refer to editions/features grid table). Use
the tabs to get access to relevant features.
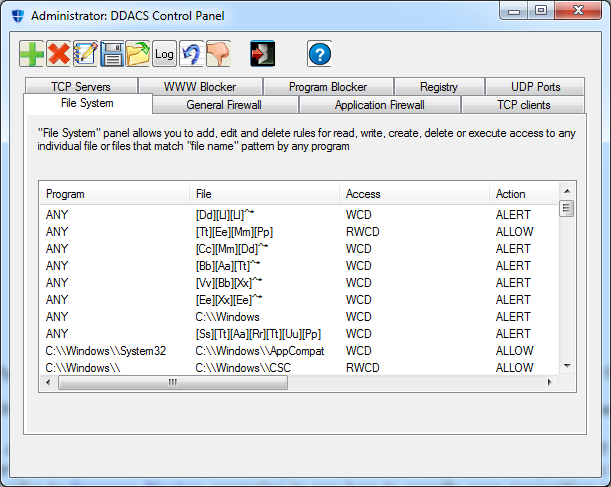
There are 9 operating
buttons: "Add", "Delete", "Edit",
"Save", "Load", "Log", "Retrieve", "Process Killer", "Help" and
"Exit" button. It's easy to distinguish them by their icons; besides,
all buttons
display a tooltip
when you stop a mouse over them.
In order to add a new rule, click on "Add" button (green
"+") and fill parameters relevant to the filter.
In order to delete a rule, select it and click on "Delete" button
(red "X"). The rule is selected by clicking on its first parameter
(here in "File System AC" it's "Program" column).
In order to edit a rule, select it and click on "Edit" button (pen
with notepad). Fill or change parameters relevant
to
the feature.
"Save" (diskette icon) and "Load" (green arrow going out of
a folder) buttons save and load rules for the current filter to/from
rules file
on disk. Each filter has its own rules file (see "Command-line Tools"
below).
"Log" button opens violation log for the feature currently used.
"Retrieve" button retrieves currently effective rules from the filter.
It's rarely needed.
"Process Killer" button opens Process Killer window.
"Help" button opens documentation.
"Exit" button quits Control Panel program.
Command-line Tools (CUI)
Command-line
tools provide an
alternative CUI interfaces and automatic load functionality. In most
aspects they
duplicate functionality of relevant control panel filters, with summary
of
differences appearing below.
The control panel is the most convenient tool to add, remove and
manipulate
rules. Command-line tools are mostly intended to be used in start-up or
installation
scripts.
There are three command-line programs: "nf.exe" (Network Filter),
"nfp.exe" (Application Firewall) and
"ff.exe" (Files Filter).
nf has
the following command-line usage:
nf - DDACS
network packet filter and related functionality management utility
One of command options (-s, -r, -R, -rp,
-c, -S, -save, -l, -log, -clear_log, -ver, -help, -h, -?) must be
specified.
Usage: nf -panel_id N {-s rule_number|-r|-R rule_number|-l|-c
command_file|-log|-clear_log|{-S|-save} command_file} [{-m | -m!}
pattern] -panel_id <id> [-pass <password>]
-s: set a
rule
-r: remove
a rule
-R: remove
a rule by number
-l: list
all rules
-m:
specify pattern to match in payload (must be enclosed in "")
-m!:
specify pattern to match not in payload (must be enclosed in "")
-c:
specify command file to read rules
-panel_id
(req): specify panel (CP tab) and feature
ID to associate with the rule. 1=file system 2=general
firewall 4=application firewall 5=TCP
clients 6=TCP servers 7=website blocker
8=programs blocker 10=registry 12=UDP
ports
-log: show
events log
-clear_log: clear events log
-S, -save:
specify command file to save rules (old file is saved with ".bak"
extension)
-stats:
get stats
-level:
specify rule's level (0 - default)
-pn: give
policy name to a rule
-rp:
delete all rules that implement a policy
-ver: get
version
-pass
<password>: provide
password from command line (must be embraced with <>)
-help, -h, -? [option] (command
option): show help, possibly for specific
option
"-s" and "-r" are interactive commands, they will ask you
for all relevant parameters. You may input "any" instead of actual
parameter (where applicable: source and destination address, source and
destination port, protocol). For source and destination addresses you
may put
"default" for default your computer's address. Please refer to
Website
Blocker and General
Firewall for details.
For protocol type "ip", "icmp", "tcp",
"udp" or "any".
"-c" option is used to load rules from a file. In order to be
consistent with the control panel, use "ddacs-nf.rul"
for general firewall rules and "ddacs-web-block.rul"
for WWW Blocker rules. Note that rules in "ddacs-web-block.rul"
must follow very special convention; refer to Website
Blocker for details.
"-panel_id" option lets
you specify panel
(CP tab) ID. CP tabs manipulate only rules designated to them. Use
"-panel_id 2" for rules designated
for general firewall
and "-panel_id 7" for
rules designated for
WWW Blocker.
You may notice that there are more rules listed by "nf"
than by CP. This is because when you specify
domain name as either source
or destination address, the rule must match all IP
addresses that this host is translated to. Since the Network Filter
operates on packet level, it needs to have a rule per each IP address.
When "nf" or control
panel upload a rule, they upload a rule for each IP address
. Consequently, there is an additional
difference: when you
delete rules for a domain with "nf
-R" or
"nf -r" you have to
remove every IP rule
that belongs to it. DDACS Control Panel does it automatically.
ff has the
following command-line usage:
ff - DDACS files filter and general management utility
No command is specified.
Usage: ff -panel_id N -s [-time] [-level
<N>] [-pn policy_name] | -r | -R rule_number | {-ra | -Ra
| -rp policy_name} | -l [-a] | -c command_file | {-S|-save}
command_file | -log | -clear_log} | -ver | -U | -t | -self_protect |
-list_proc {-help | -?} | -suspend pname | -resume pname | -suspend_pid
pid | -resume_pid pid | -list_proc | -kill pid [-reg] [-pass
<password>] [-u]
-s: set a
rule
-time: use
start/end time (when setting a rule)
-r, -R:
remove a rule by number
-ra, -Ra:
remove all rules
-l: list
rules
-a: list
all rules (including invisible and permanent)
-c:
specify command file to read rules
-S, -save:
specify command file to save rules (old file is saved with ".bak"
extension)
-panel_id
(req): specify panel (CP tab) and feature
ID to associate with the rule. 1=file system 2=general
firewall 4=application firewall 5=TCP
clients 6=TCP servers 7=website blocker
8=programs blocker 10=registry 12=UDP
ports
-log: show
events log
-clear_log: clear events log
-reg:
operate registry key rather than files
-suspend:
suspend all instances of a program
-resume:
resume all instances of a program
-suspend_pid: suspend a process by PID
-resume_pid: resume a process by PID
-list_proc: list running processes
-kill:
terminate a process by PID
-t:
terminate agent
-U: allow
driver unload
-restore_defrules: restore default rules
-level:
specify rule's level (0 - set defaults)
-pn: give
policy name to a rule
-rp:
delete all rules that implement a policy
-self_protect: reload internal self
protection rules
-ver: get
version
-pass
<password>: provide
password from command line (must be embraced with <>)
-help, -h, -? [option] (command
option): show help, possibly for specific
option
As it immediately appears, the options are very similar to those of
"nf" and they have the same
meaning. Please refer to
Files
Access Filter and
Programs
Blocker
for details.
"-c" option is used to load rules from a file. In order to be
consistent with the control panel, use "ddacs-ff.rul"
for general files access rules and "ddacs-prog-block.rul"
for Program Blocker rules. Note that rules in "ddacs-prog-block.rul"
must follow very special convention; refer to Programs
Blocker for details.
"-panel_id" option lets
you specify panel
(CP tab) ID. CP tabs manipulate only rules designated to them. Use
"-panel_id 1" for rules designated
for general files
access control and "-panel_id
8" for rules
designated for Program Blocker.
nfp has the
following command-line usage:
nfp - DDACS application forewall filter and related
functionality management utility
Usage: nfp {-s|-r|-R
rule_number|-l|-log|-clear_log|{-S|-save} command_file} [-m "pattern"]
-s: set a
rule
-r: remove
a rule
-R: remove
a rule by number
-l: list
all rules
-p: get
list of processes and upload them to driver
-m:
specify pattern to match in payload
-c:
specify command file to read rules
-panel_id
(req): specify panel (CP tab) and feature
ID to associate with the rule. 1=file system 2=general
firewall 4=application firewall 5=TCP
clients 6=TCP servers 7=website blocker
8=programs blocker 10=registry 12=UDP
ports
-log: show
events log
-clear_log: clear events log
-S, -save:
specify command file to save rules (old file is saved with ".bak"
extension
-level: specify rule's level (0 - default)
-pn: give
policy name to a rule
-rp:
delete all rules that implement a policy
-time: set
time constraints for program's usage
-hosts_bl:
set host blacklist rule
-pass
<password>: set password
from command line (must be embraced with <>)
-l may be used with -s or -r
The
meaning of options is similar to options of "ff" and "nf" programs.
"-s" and "-r" options are interactive and will require input of rule
details.
The
table below summarizes correspondence of parameter to "-panel_id"
argument to installed feature and default rules file. You should use
correct parameter in order for relevant feature to operate correctly.
Default rules file is what is automatically loaded for each feature
when the system starts (if you answered "yes" to an "Automatic Start"
question during installation) and what is loaded and saved by GUI
programs. Using command-line tools you can load additional files for
every feature.
| Panel ID |
Feature |
Default Rules File |
| 1 |
Files Access Control |
ddacs-ff.rul |
| 2 |
General Firewall |
ddacs-nf.rul |
| 4 |
Application Firewall |
ddacs-nfp.rul |
| 5 |
TCP Clients Rules |
ddacs-tcp-client.rul |
| 6 |
TCP Servers Rules |
ddacs-tcp-server.rul |
| 7 |
Website Blocker |
ddacs-web-block.rul |
| 8 |
Programs Blocker |
ddacs-prog-block.rul |
| 10 |
Registry Access Rules |
ddacs-reg.rul |
| 11 |
Processes Access Rules |
ddacs-proc.rul |
| 12 |
UDP Ports Rules |
ddacs-udp-ports.rul |
Features and Editions
The table
below specifies which features are included in what editions.
|
Free |
Total
Admin |
| General
Firewall |
Yes |
Yes |
| Application
Firewall |
No |
Yes |
| Files
Access Control |
Yes |
Yes |
| Website
Blocker |
Yes |
Yes |
| Program
Blocker |
Yes |
Yes |
| Registry
Access Control |
No |
Yes |
| Process
Killer |
No |
Yes |
| TCP
Clients Rules |
No |
Yes |
| TCP
Servers Rules |
No |
Yes |
| UDP Ports
Rules |
No |
Yes |
Recommendations
Access
control rules are so
different that it's hard to offer specific recommendations. We will
attempt
however, to provide general recommendation without claiming that we
know the
user's needs better.
- In many cases a
simple strategy "block everything" /
"allow specific exceptions" is suitable. DDACS
filters provide general rules where almost all paramters may be
specified as any.
This includes "any protocol", "any destination port" in Network Filter
and "any accessor
program" in Files Access Filter
- A general rule may
be created along with a single exception, with the help of decision
inversion options. Decision inversion is applied to any
specific rule and the meaning is turned to "any BUT this parameter will
match". E.g. Network Filter rule: "TCP" as protocol with option
"any but this" checked, "any" source and destination address and action
"block" will actually block any non-TCP traffic.
Decision inversion rules are used on specific rules;
don't use them with general rules. E.g. despite specification of
"any" protocol and "any but this" is legal,
it creates a senseless rule that matches no possible packet.
- Use patterns
in Network Filter moderately, think well relevant policies and affect
on system
performance and communications
- On
the contrary, in Files Filter it is preferable to use patterns for
programs and file names. Using patterns or partial names may allow to
implement the same policy with less rules, which will save system
resources and allows better performance: less rules require
less memory
and less time to check
- It is generally
recommended to start DDACS at system startup and apply automatic rules
at startup. It is convenient, since use of the same computer will not
change frequently, the basic rules set needs not to also. Automatic
rules upload offers protection from that point on
- If you don't find
it easy to find optimal rules set, you may change rules and save them
frequently at first. In this case it is also beneficial to start rules
at startup, that will
give to the best picture on how they protect and how they affect
performance.
- When
you have a program that you suspect on unwanted behavior, you
may want
to run it in a sort of sandbox. Run it with most system-relevant file
accesses blocked and with most network access blocked, and don't run
any other networking programs. Thus you don't allow its unwanted
behavior and study what it attempts to do via violation log.
Alternatively you may install a rule with "prompt" action for any
system-relevant file access for that program. When you make sure with
logs that the program does nothing unwanted, you may allow it access to
system resources one by one by installing appropriate "allow" rules or
removing "block" rules
Interoperability
System
Requirements
DDACS can protect Windows 7
or newer Windows operating
systems.
Interoperability
with Other Security Software
DDACS is based on its kernel-mode
filters, and their
rules-based policy enforcement. It doesn't register within the OS as
security
solution, so it doesn't have interoperability
issues with other software, including security packages.
You should remember however, that rules enforcement actually adds a
tiny bit of
additional processing on every file or network access. Other security
packages
may in some cases do the same, some adding more
heavy processing,
some less. Consequently, every security package adds toll on
system
performance, depending on its functionality and optimization. In order
to get
the best performance on a protected system you should design protection
schemes
from different packages so that you don't run the same filtering
several
times.
References
