Daniel Drubin Access Control Suite Getting Started Guide
This manual provides quick-start guidance to Daniel Drubin
Access Control Suite
(ACS).
This document relates to release version 1.0
Installing DDACS
Installation
of DDACS is easy.
Download a self-extracting installer package suitable for your
operating
system, run it and follow the installation instructions. The
installation asks
only three questions:
- About installation
directory (default is "c:\Program Files\Daniel Drubin ACS")
- If you want to
install default rules set
- If you want to
start DDACS automatically
If you install on Windows XP, you
will see several times a
Windows warning box popping up and saying that "DDACS Miniport Driver
is
not signed", then warn you about risks of using unsigned drivers. DDACS
doesn't include a real hardware driver, but in order to filter network
traffic
it installs an NDIS intermediate driver. Its outbound part is
recognized by XP
as hardware driver (which is incorrect), causing it to display this
prompt.
There is no such warning on later versions of Windows.
If you install on Windows Vista and later, you will receive a prompt
telling
that the installer requests administrator privileges and if you agree
to grant
it. Since DDACS installs and operates system-level components, it has
to be
installed with administration privileges; otherwise the suite will not
function.
If you ever want to uninstall DDACS, simply run "uninstall.exe"
from DDACS start menu or use Windows Control Panel "Add/Remove
Programs" to uninstall.
Using DDACS
This chapter describes DDACS
essentials and configuration
tools and files.
DDACS Control Panel (GUI)
DDACS Control Panel is the most
convenient way to create and
manipulate rules. It has four tabs: "File System AC", "General
Firewall", "WWW Blocker" and "Program Blocker". Use
the tabs to get access to relevant filters.
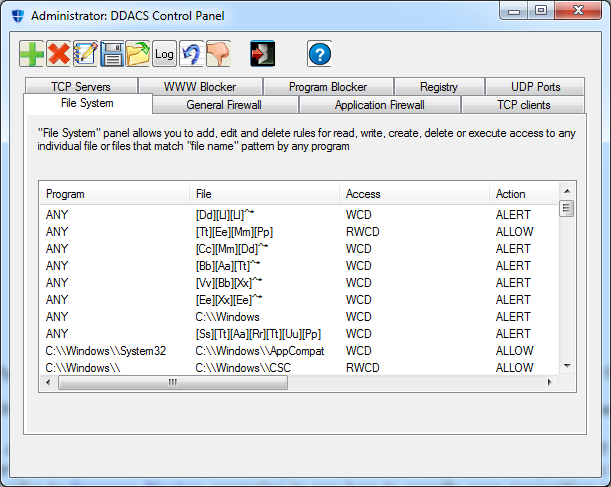
There are five rules operating buttons: "Add", "Delete", "Edit", "Save"
and "Load" and
"Exit" button. It's easy to distinguish them by their icons; besides
that all bottons
display a tooltip
when you stop a mouse over them.
In order to add a new rule, click on "Add" button (green
"+") and fill parameters relevant to the filter.
In order to delete a rule, select it and click on "Delete" button
(red "X"). The rule is selected by clicking on its first parameter
(here in "File System AC" it's "Program" column).
In order to edit a rule, select it and click on "Edit" button (pen
with notepad). Fill or change parameters relevant
to
the filter.
"Save" (diskette icon) and "Load" (green arrow going out of
a folder) buttons save and load rules for the current filter to/from
rules file
on disk. Each filter has its own rules file (see "Command-line Tools"
below).
Command-line Tools (CUI)
Command-line
tools provide an
alternative CUI interfaces and automatic load functionality. In most
aspects they
duplicate functionality of relevant control panel filters, with summary
of
differences appearing below.
The control panel is the most convenient tool to add, remove and
manipulate
rules. Command-line tools are mostly intended to be used in start-up or
installation
scripts.
There are two command-line programs: "nf.exe" (Network Filter) and
"ff.exe" (Files Filter). "nf"
has
the following command-line usage:
nf{-s|-S rule_number|-r|-R
rule_number|-l|-c command_file}
[-m "pattern"] [-panel_id
id]
-s: set a rule (you will be asked
for all parameters)
-S: set a rule with specified number
(all following rules shift)
-r: remove a rule (you will be asked
for all parameters; only a rule that is exactly equal will be removed)
-R: remove a rule by number (use
"-l" in order to get rules numbers)
-l: list all rules (with order
numbers)
-m: specify pattern to match
(assumes "-s")
-c: specify command file to read
rules
-panel_id:
specify panel (CP
tab) ID to associate with the rule
-l may be used with -s or -r
or
separately
"-s" and "-r" are interactive commands, they will ask you
for all relevant parameters. You may input "any" instead of actual
parameter (where applicable: source and destination address, source and
destination port, protocol). For source and destination addresses you
may put
"default" for default your computer's address.
For protocol type "ip", "icmp", "tcp",
"udp" or "any".
"-c" option is used to load rules from a file. In order to be
consistent with the control panel, use "firewall.rul"
for general firewall rules and "web-block.rul"
for WWW Blocker rules.
"-panel_id" option lets
you specify panel
(CP tab) ID. CP tabs manipulate only rules designated to them. Use
"-panel_id 2" for rules designated
for general firewall
and "-panel_id 7" for
rules designated for
WWW Blocker.
You may notice that there are more rules listed by "nf"
than by CP. This is because:
- "nf" lists all the
rules for both general firewall and website blocker
- When you specify
domain name as either source
or destination address, the rule must match all IP
addresses that this host is translated to. Since the Network Filter
operates on packet level, it needs to have a rule per each IP address.
When "nf" or control
panel upload a rule, they upload a rule for each IP address
Consequently, there is an additional
difference: when you
delete rules for a domain with "nf
-R" or
"nf -r" you have to
remove every IP rule
that belongs to it. DDACS Control Panel does it automatically.
"ff" has the following command-line usage:
ff {-s|-r|-R rule_number|-l|-c
command_file}
[-m "pattern"] [-panel_id
id]
-s: set a rule
-r: remove a rule
-R: remove a rule by number
-l: list all rules
-p: get list of processes and upload
them to driver
-c: specify command file to read
rules\n"
-panel_id:
specify panel (CP
tab) ID to associate with the rule
-l may be used with -s or -r
As it immediately appears, the options are very similar to those of
"nf" and they have the same
meaning.
"-c" option is used to load rules from a file. In order to be
consistent with the control panel, use "ff.rul"
for general files access rules and "prog-block.rul"
for Program Blocker rules.
"-panel_id" option lets
you specify panel
(CP tab) ID. CP tabs manipulate only rules designated to them. Use
"-panel_id 1" for rules designated
for general files
access control and "-panel_id
8" for rules
designated for Program Blocker.
Default Configuration
Default configuration is stored in
Rules files and may be
loaded at system start-up or reloaded from disk at any time. DDACS
comes with
default rules set that may be modified at any time later.
Default rules are:
- WWW Blocker, Files Access Control and Program Blocker empty
- General Firewal:
- All UDP traffic blocker
- UDP exceptions:
- outbound from default:any
port to any address:53 and inbound from any address:53 to default:any
port (DNS)
- outbound from default:any
port to any address:5355 and inbound from any address:5355 to default:any
port (DNS extensions on newer Windows versions starting from Vista)
- outbound from default:137 to any address:137 and inbound from any address:137 to default:137
port (NetBIOS)
- outbound from default:138 to any address:138 and inbound from any address:138 to default:138
port (NetBIOS)
- outbound from default:139 to any address:139 and inbound from any address:139 to default:139
port (NetBIOS)
- All TCP inbound connections are blocked (packets with TCP SYN)
- All outbound TCP connecitons are blocked
- TCP exceptions:
- outbound from default:any
port to any address:25 and inbound from any address:25 to default:any
port (SMTP)
- outbound from default:any
port to any address:80 and inbound from any address:80 to default:any
port (WWW)
- outbound from default:any
port to any address:110 and inbound from any address:110 to default:any
port (POP3)
- outbound from default:any
port to any address:143 and inbound from any address:143 to default:any
port (IMAP)
- outbound from default:any
port to any address:443 and inbound from any address:443 to default:any
port (HTTPS)
- outbound from default:any
port to any address:445 and inbound from any address:445 to default:any
port (Microsoft DS)
Recommandations
Access
control rules are so
different that it's hard to offer specific recommendations. We will
attempt
however, to provide general recommendation without claiming that we
know the
user's needs better.
- In most cases a
simple strategy "block everything" /
"allow specific exceptions" is suitable. DDACS
filters provide aggregate rules where almost all paramters may be
specified as any.
This includes "any protocol", "any destination port" in Network Filter
and "any accessor
program" in Files Access Filter
- A general rule may
be created along with a single exception, with the help of decision
inversion options. Decision inversion is applied to any
specific rule and the meaning is turned to "any BUT this parameter will
match". E.g. Network Filter rule: "Protocol:TCP" with option
"any but this" checked, "any" source and destination address and action
"block" will actually block any non-TCP traffic.
Decision inversion rules are used on specific rules;
don't use them with aggregate rules. E.g. despite specification of
"any" protocol and "any but this" is legal,
it creates a senseless rule that matches no possible packet.
- Use patterns
moderately and think well relevant policies and affect on system
performance and communications
- It is generally
recommended to start DDACS at system startup and apply automatic rules
at startup. It is convenient, since use of the same computer will not
change frequently, the basic rules set needs not to also. Automatic
rules upload offers protection from that point on.
- If you don't find
it easy to find optimal rules set, you may change rules and save them
frequently at first. In this case it is also beneficial to start rules
at startup, that will
give to the best picture on how they protect and how they affect
performance.
References
