|
Element
|
Meaning
|
|
.
|
Any single character matches
|
|
[xyz]
|
Any of the characters embraced
in square brackets matches a single character. Any character not in set
doesn't match
|
|
^x
|
Any character except x matches
("x" here is some single character)
|
|
[^xyz]
|
Any character except any
character belonging to set matches ("x" here is some single character)
|
|
?x
|
"x"
appearing 0 or 1 times matches ("x" here is some single character). The
meaning of this construct is in matching "x" if it appears, so that the
next character in search set is compared to a character after "x"; if
"x" doesn't appear in search set in this
positions then it is considered as appeared 0 times and
that character is compared to the next character in argument string.
|
|
*x
|
"x"
appearing 0 or more times matches ("x" here is some single character).
The meaning of this construct is in matching "x" if it appears, so that
the next character in search set is compared to a character after "x";
if "x" doesn't appear in search set in this
positions then it is considered as appeared 0 times and
that character is compared to the next character in argument string.
"*x" matches any number of repeated "x" characters
|
|
+x
|
"x"
appearing 1 or more times matches ("x" here is some single character).
The meaning of this construct is in matching "x" if it appears, so that
the next character in search set is compared to a character after "x";
if "x" doesn't appear in search set in this
positions then the matching fails. "*+" matches any number
of repeated "x" characters, but no less tha
1.
|
|
\
|
Backslash has a special
meaning. It is an escape character, which allows
specification of characters that are non-printable or otherwise hard to
specify.
- "'\\" means
a single backslash character
- "\r" is
"carriage return (ASCII 13)
- "\n" is "new
line" (ASCII 10)
- "\t" is
"tabulation" (ASCII 8)
- "\xHH" is a character specified by
its ASCII code in hexadecimal ("\" ad "x" are literally backslash and
"x", and "HH" are two hexademal
digits (their ASCII codes).
- "\" followed
by any other character means matching a single appearance of
that character (the same effect
as if "\" did not appear). This is important in order to type symbols
that are used
for control when not escaped: '.', '[', ']', '^', '*', '+', '?'
|
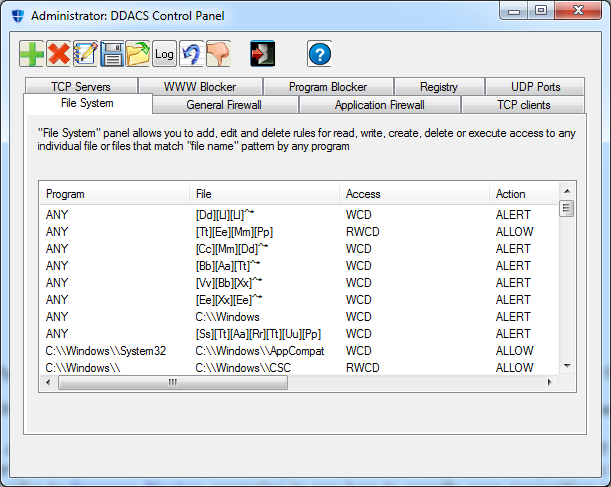
![[ddacs_cp_www.png]](images/ddacs_cp_www.png)
![[ddacs_cp_add_www.png]](images/ddacs_cp_add_www.png)
![[ddacs_cp_genfw.png]](images/ddacs_cp_genfw.png)
![[ddacs_cp_add_genfw.png]](images/ddacs_cp_add_genfw.png)
![[ddacs_cp_prog.png]](images/ddacs_cp_prog.png)
![[ddacs_cp_add_prog.png]](images/ddacs_cp_add_prog.png)
![[ddacs_cp.png]](images/ddacs_cp.png)
![[ddacs_cp_add_ff.png]](images/ddacs_cp_add_ff.png)